Security standards, in all their various shapes and forms, are often viewed as a deep well of compliance nit-noid details associated with ever-rising demands on resources and periodic compliance and audit agonies. But let’s step beyond the agony to recognize and make effective use of security standards as the rich source of security knowledge they represent.
Standards – Information
Information Security standards cover a wide range of topics, from the general to the specific. ISO 27000 is a family of 19 standards incorporating requirements, general guidelines, and sector-specific guidelines addressing a wide range of security concerns.
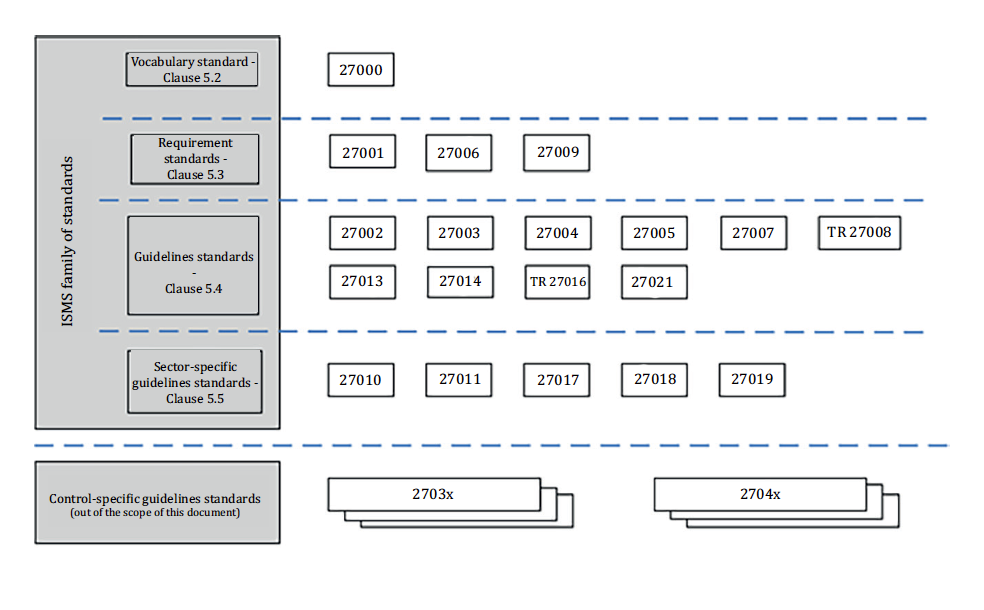
ISMS family of standards relationships – ISO/IEC 270001
Information Security standards have some form of structural framework to organize standards elements, usually explicitly defined within the standard.
NIST’s Risk Management Framework is supported by a comprehensive collection of standards and guidelines, including Special Publication 800-53 Rev. 5, Security and Privacy Controls for Information Systems and Organizations. The NIST controls are presented using a consistent structure that facilitates identifying and using the control information elements.

NIST 800-53 Rev. 5 Control Structure 2
The International Electrotechnical Commission is producing the multi-standard IEC 62443 series of standards focused on the specific subject of cyber security of industrial automation and control systems.

ISA/IEC 62443 series of IACS standards and technical reports 3
These and other standards capture detailed and often specialized information security information and knowledge. This knowledge can be leveraged by any organization to cost-effectively improve their security.
ENISA, the European Union Agency for Cybersecurity, has noted some of the many reasons these standards play important roles in information security, including4:
- Improving the efficiency and effectiveness of key processes
- Facilitating systems integration and interoperability
- Enabling different products or methods to be compared meaningfully.
- Providing a means for users to assess new products or services
- Structuring the approach to deploying new technologies or business models
- Simplification of complex environments
- Promoting economic growth
But these information security standards bring us several challenges. First, there are many standards, some general, some very specific, from a variety of international, national, and sector sources. Second, individually and collectively, they contain an immense amount of information. Third, the correlation and often deep interplay within and between information security standards is complex and becoming more complex. Fourth, few organisations have the luxury of limiting themselves to a single security standard because they must comply with information security standards from several authorities. Still, since each security standard has its own strengths and weaknesses and few are comprehensive, it makes sense to draw on the standards that provide real value. There’s gold in those standards, if we can mine it effectively.
So, while information security standard brings us an embarrassment of riches, we must face the overarching challenge of transforming the wealth of security information into relevant and useful information knowledge by making it useful to our organisations. We can extract the value we need by aligning and integrating the security information into our organisations when and where it will deliver business-enabling value.
Security Standards – Using SABSA to Transform Information into Knowledge
The SABSA Framework and Methodology includes several elements that help align and integrate information security standards into a holistic, coherent enterprise security framework. Let’s take a quick look at four SABSA’s Knowledge Management Framework, the SABSA Architecture and Management Matrices, SABSA’s Layer Mapping Technique, and, of course, SABSA Attributes.
SABSA is an Enterprise Security Architecture Knowledge Management Framework that helps improve the quality of decision making by ensuring that reliable information is available throughout the information security service lifecycle.
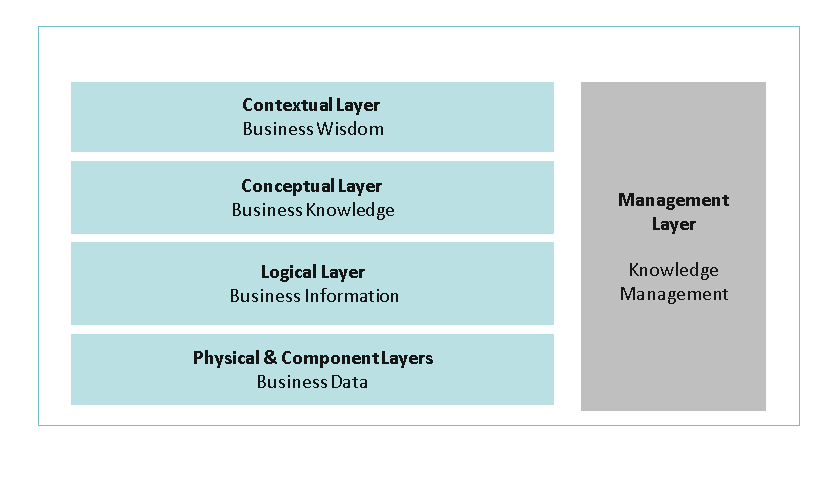
SABSA Knowledge Management Framework 5
SABSA’s management activities aggregate and contextualize knowledge through the SABSA Matrices’ Architecture layers to ultimately deliver the wisdom we need to succeed.
The SABSA Architecture and Management Matrices provide enterprise security architecture elements in a coherent framework into which any security standard, guideline, or method can be mapped. For example, security management strategies, control objectives, and control libraries, as artefacts, map to the Motivation column in the Conceptual Architecture Layer.

Mapping Information Security Standards Management, Controls Objectives, and Control Libraries to the SABSA Architecture Matrix
Control libraries from any relevant and useful standard are, in turn, mapped and distributed to relevant cells within the architecture matrices.
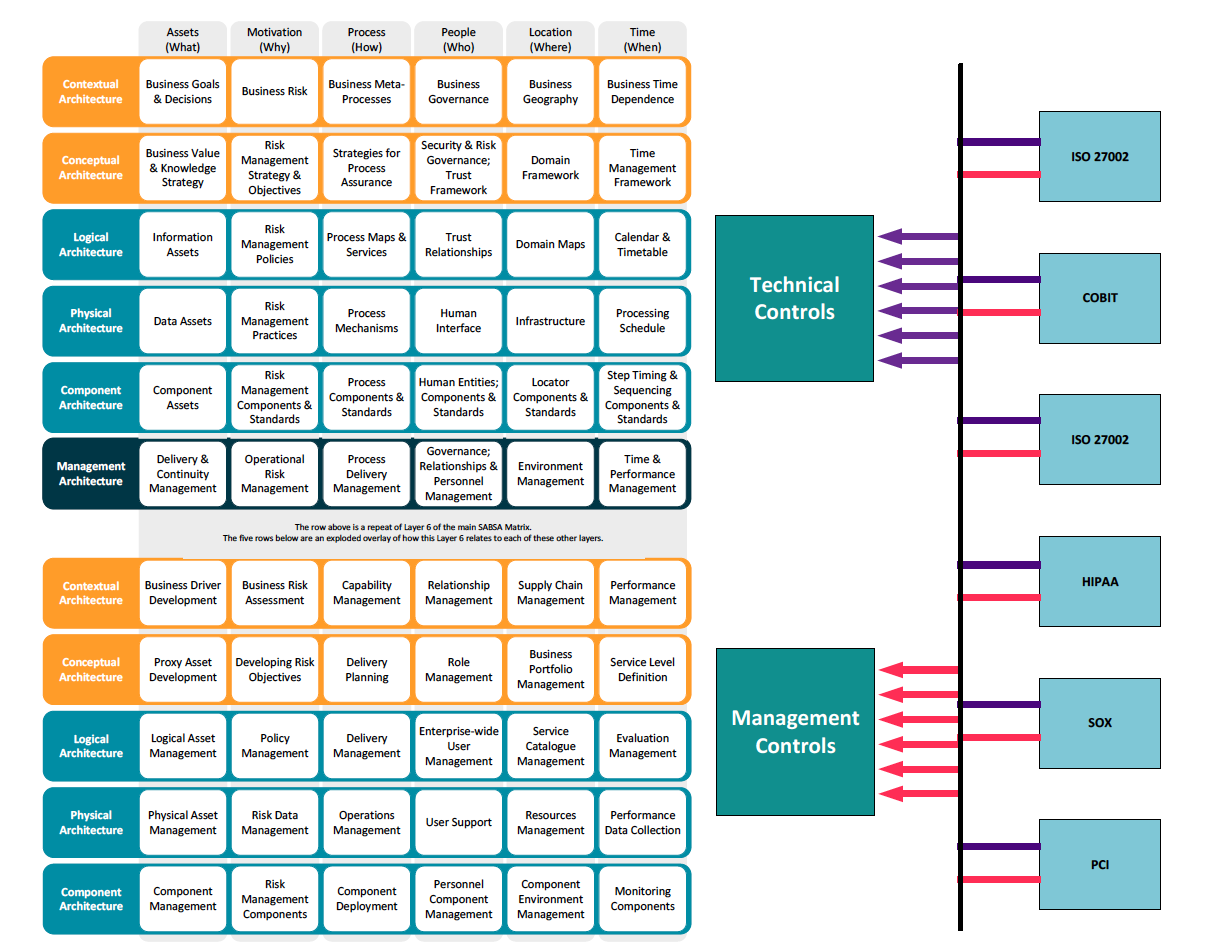
Aligning and integrating Controls Frameworks & Libraries to the SABSA Matrices
SABSA’s Layer-Mapping Technique provides a mechanism to align and link architectural elements from architecture layer to architecture layer, establishing full two-way traceability between all architecture layers to deliver knowledge for:
- Asset risk status
- Asset risk & enablement performance
- Re-usability of assets to meet control & enablement objectives
- Completeness, justification & assurance
- Managing change

SABSA’s Layer Mapping Technique 6
SABSA Attributes provide the required collection of linchpins that allow us to align and integrate the information captured in relevant standards and guidelines into an organization’s evolving enterprise security architecture. We map scope-relevant sets of attributes to the enterprise-relevant security control standards into our enterprise security architecture.
This alignment and integration enable us to leverage the wealth of security information contained in the security standards by transforming information security information into information security knowledge. Why re-invent all those wheels? We can transform security information developed by hundreds of security experts from around the world into information security knowledge of direct value to our organizations. Use that knowledge to ensure to improve the quality of decision making.
1ISO/IEC 27000. Information technology — Security techniques — Information security management systems. Overview and vocabulary, 5th Edition. 2018-02. Page 19.
2NIST SP 800-53 Rev. 5, Security and Privacy Controls for Information Systems and Organizations. September 2020; updated Dec. 10, 2020. Page 9.
3https://www.isa.org/standards-and-publications/isa-standards/isa-standards-committees/isa99
4Steve Purser. Standards for Cyber Security. European Union Network and Information Security Agency (ENISA). 2014.
5, 6The SABSA Institute



